North Korea (DPRK) Attack
If you’ve been sent this document, then we have very good reason to believe that you have been hacked by North Korea (DPRK). This document will give you some information about North Korea, why they’ve hacked you, and how they might’ve done it.
BEFORE YOU CONTINUE FOLLOW THIS GUIDE TO PROTECT YOUR ASSETS: Malware Infection
North Korea is an extremely isolated country that has increasingly relied on cybercrime in order to generate revenue for itself. In 2024, North Korea stole an estimated 1.34 billion USD from the cryptocurrency industry alone, and in February of 2025, North Korea stole 1.5 billion USD from Bybit exchange.
North Korea operates a few different hacking squads, one of which we believe is responsible for compromising your computer. Each squad has their own preferred methodology, but their end goal is all the same: to steal your private keys and your login information.
If you have been infected by North Korean malware, you should assume your private keys, files, and online accounts have all been stolen. North Korean hackers may then use your accounts to impersonate you and hack your contacts.
Here are some of the more recent ways we’ve seen North Korea hack people.
The Fake Video Conference Software
In this method, the hackers will impersonate a person that you know or are likely to trust, like an investor. They will send you a link to a video call, but it will not be Google Meet, Zoom, Microsoft Teams, or some other common software. Instead, the domain will be something entirely different.

A message sent by a North Korean hacker impersonating an investor
When you visit this link and try to join the call, you will encounter an “error” and be prompted to fix it yourself.
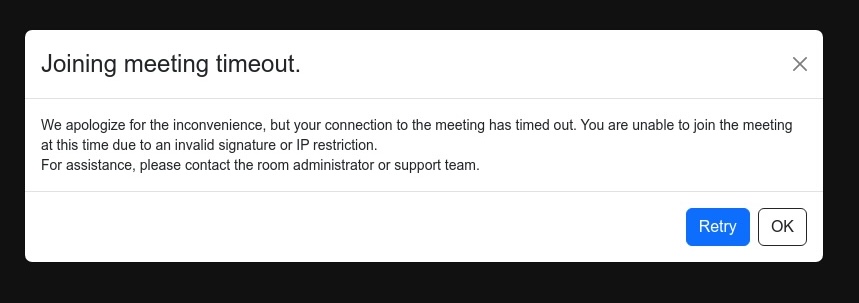
A fake error shown by the North Korean website
The instructions that you are provided will install malware on your computer.
The Fake PDF
In this method, you are sent a link to download a report, slide deck, or other plausible document.
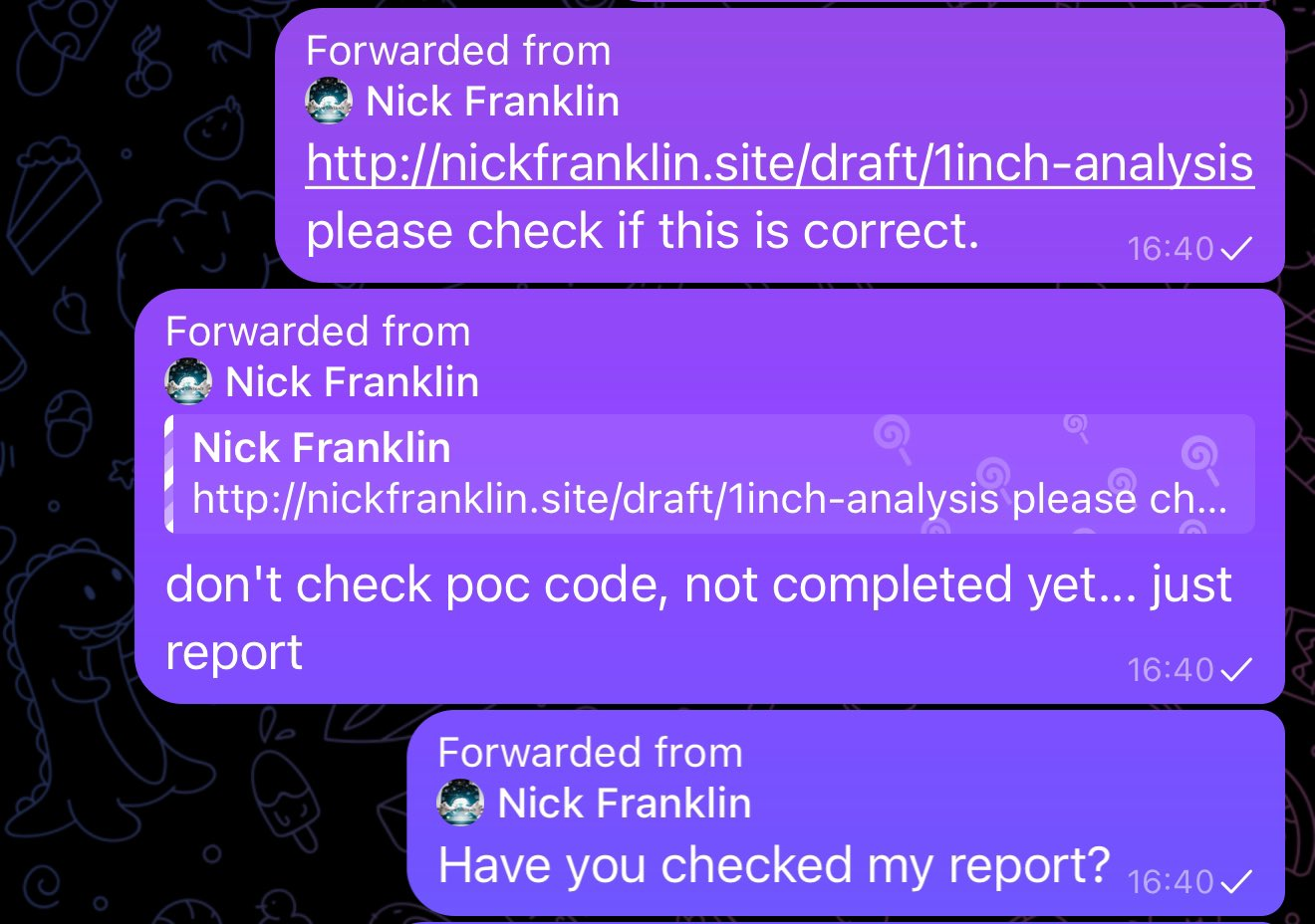
An example of a North Korean hacker attempting to share a link to malware
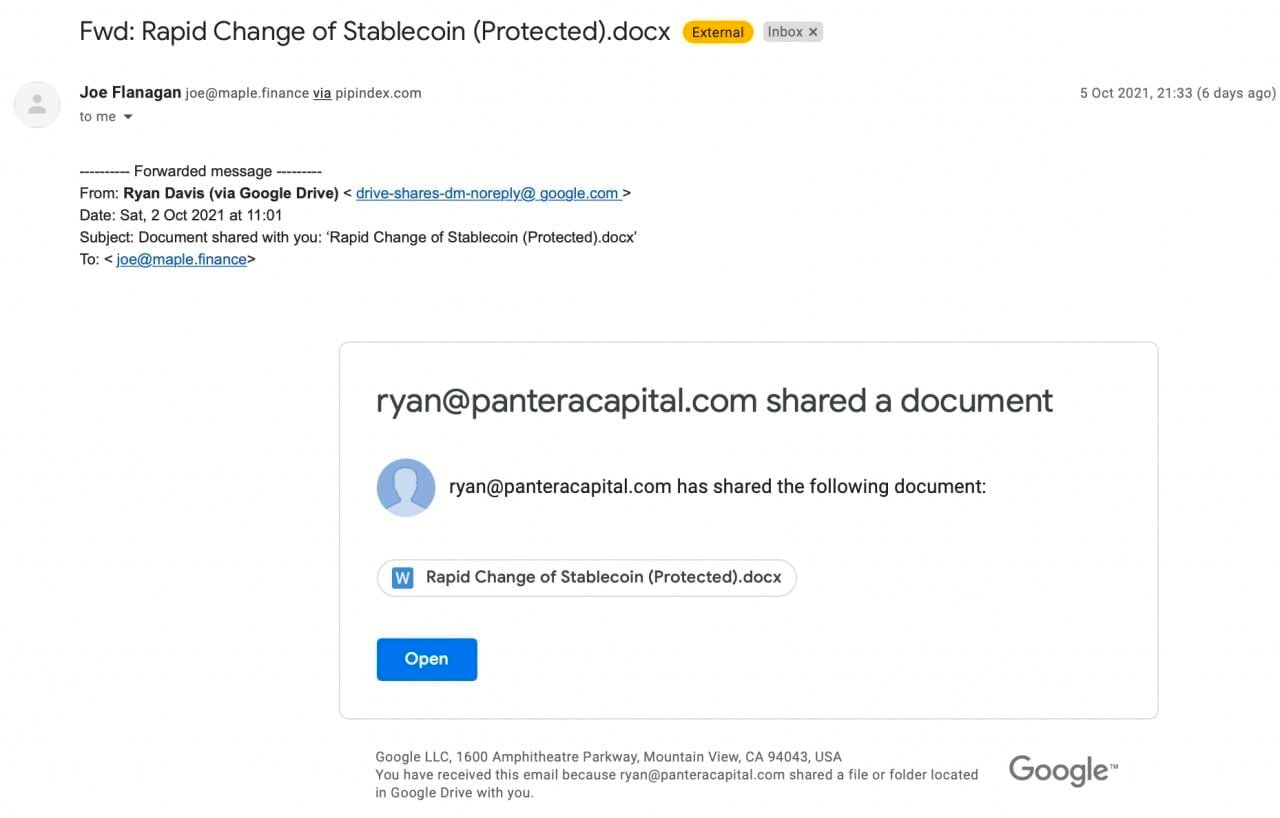
An older example of a North Korean phishing email
If you download and run this file, you will have executed the malware. The first thing the malware does is open the PDF file you were expecting, so that you do not suspect you were infected.